Over the past few years, owners of cars with keyless start systems have learned to worry about so-called relay attacks, in which hackers exploit radio-enabled keys to steal vehicles without leaving a trace. Now it turns out that many millions of other cars that use chip-enabled mechanical keys are also vulnerable to high-tech theft. A few cryptographic flaws combined with a little old-fashioned hot-wiring—or even a well-placed screwdriver—lets hackers clone those keys and drive away in seconds.
Related: Tesla and McLaren’s Keyless Entry System Could Be Hacked Within Seconds
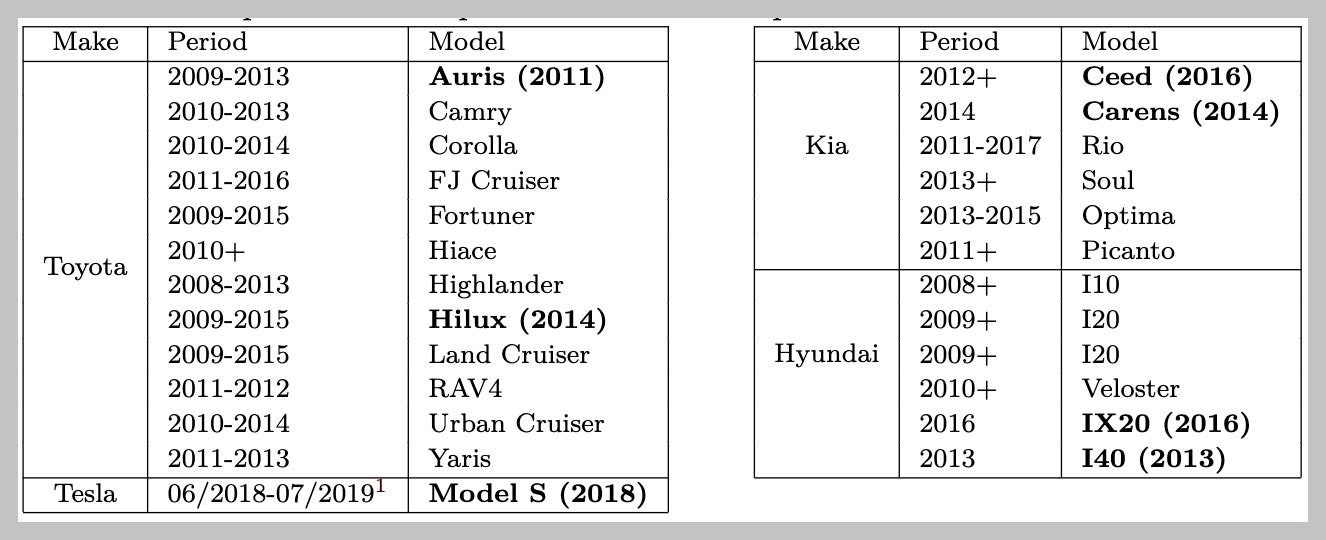
Earlier this week, researchers from KU Leuven in Belgium and the University of Birmingham in the UK revealed new vulnerabilities they found in the encryption systems used by immobilizers, the radio-enabled devices inside of cars that communicate at close range with a key fob to unlock the car’s ignition and allow it to start. Specifically, they found problems in how Toyota, Hyundai, and Kia implement a Texas Instruments encryption system called DST80. A hacker who swipes a relatively inexpensive Proxmark RFID reader/transmitter device near the key fob of any car with DST80 inside, can gain enough information to derive its secret cryptographic value. That, in turn, would allow the attacker to use the same Proxmark device to impersonate the key inside the car, disabling the immobilizer and letting them start the engine.
The researchers say the affected car models include the Toyota Camry, Corolla, and RAV4; the Kia Optima, Soul, and Rio; and the Hyundai I10, I20, and I40. Below is the full list of vehicles that the researchers found to have the cryptographic flaws in their immobilizers:
Though the list also includes the Tesla S, the researchers reported the DST80 vulnerability to Tesla last year, responding to which the company had pushed out a firmware update that blocked the attack.
Related: Car-Hacking Is The Biggest Threat To Automobiles
The trick is done by reverse-engineering the cipher that Texas Instruments is keeping a secret since the release of the DST80. The problem is that car manufacturers simplified the otherwise robust anti-theft system for their convenience. For example, Toyota is using the vehicle serial number in the cryptographic key that’s transmitted. This significantly reduces the number of random bits that potential attackers would have to guess in order to reconstruct it. As for Kia and Hyundai, those two decided to use only 24 bits of randomness, essentially making it possible for someone with a mediocre laptop to be able to brute-force the key in a few milliseconds.
Researchers note that a thief could simply turn the barrel with a screwdriver or hot-wire the car’s ignition switch, just as car thieves did before the introduction of immobilizers neutered those techniques. “You’re downgrading the security to what it was in the ’80s,” says University of Birmingham computer science professor Flavio Garcia. And unlike relay attacks, which work only when within range of the original key, once a thief has derived the cryptographic value of a fob, they can start and drive the targeted car repeatedly.
Related: Nokia and FAW Signed MoU to Use 5G
Hyundai responded by saying that no cars with low-entropy keys were sold in the United States, so I guess they were meaning to say that such systems are only deployed in countries where crime rates are low? Toyota responded by stating that the vulnerability applies to older models and that their newer cars are using a different system. Contrary to Tesla, neither Toyota nor Hyundai can do anything about the vulnerability, as a firmware update wouldn’t fix the flaw. The only thing that they could do is to offer replacements for the immobilizers or the key fobs, but so far, they haven’t offered anything like that to their customers.
Even so, the researchers say that they decided to publish their findings to reveal the real state of immobilizer security and allow car owners to decide for themselves if it’s enough. Protective car owners with hackable immobilizers might decide, for instance, to use a steering wheel lock. “It’s better to be in a place where we know what kind of security we’re getting from our security devices,” Garcia says. “Otherwise, only the criminals know.”

A computer animation professional with over 23 years of industry experience having served in leading organizations, TV channels & production facilities in Pakistan. An avid car enthusiast and petrolhead with an affection to deliver quality content to help shape opinions. Formerly written for PakWheels as well as major publications including Dawn. Founder of CarSpiritPK.com